Continuous Compliance in Fast Paced Environment
The new business imperatives enabled by Cloud services namely the need for speed at scale and high velocity releases must be balanced by managing associated risks such as adhering to compliance and meeting IT security needs.
The flip side of not managing risk is obvious—it amplifies the organization’s exposure to breaches causing irreparable damage; and a single incompliance cascades into larger challenges taking that much longer to fix a lapse. Needless to say roll backs are expensive, chaotic and erodes confidence in IT processes.
Periodic security audits made sense when IT was managed the traditional way, but in the Cloud environment where deployments are dynamic—managed by auto scaling and high-velocity DevOps processes—organizations must institute practices that facilitate continuous compliance.
Cloud characteristics make adherence and compliance easier as reports are created continuously and lapses are highlighted immediately. The window between vulnerability identification and rectification has reduced and can be acted on a continuous basis.
This can be achieved by codifying compliance wherein infrastructure is pre-configured and environments are always compliant during staging processes and even as it scales. Close and continuous monitoring ensures compliance by sending notifications in case of breach or non-compliant activity, accompanied by auto-remedial measures including denying access to non-compliant resources and auto-correction of specific conditions.
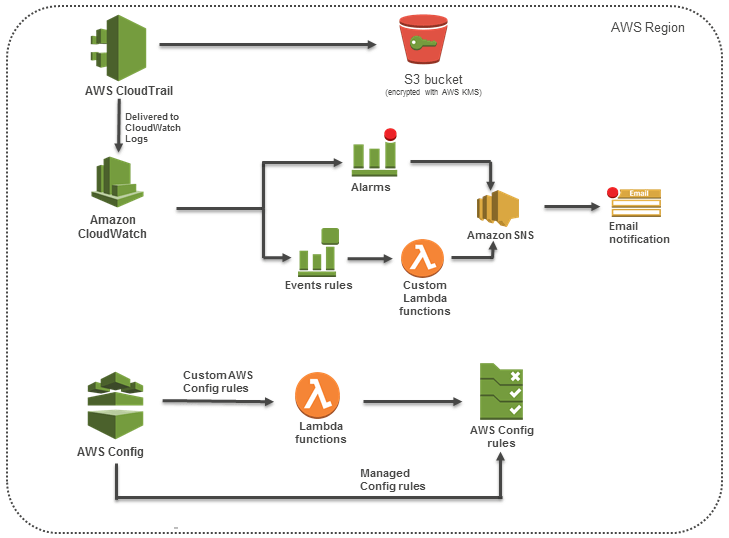
Noventiq has helped many organizations achieve continuous compliance in the AWS Cloud using Well-architected framework and AWS services such as Config, AWS CloudTrail and Lambda.
A global smartphone manufacturer wanted to achieve continuous compliance while taking advantage of the scalability of AWS and enabling multiple teams to work collaboratively. We took the following steps to enable continuous compliance:
- First we documented security requirements at different levels and created detailed checklist of security groups, ACLs, IAM, VPC and subnets, tagging resources, etc.
- Next we automated configuration management, deployment and change using Cloud Formation, Ansible, AWS Inspector and Systems Manager.
- We scripted templates for AMI, defined resources, instance type and size, database configuration and created templates with security details such as server hardening, firewall configuration, back up and log management policies.
- Enabled close monitoring and rigorous adherence with AWS Config and Cloud Trail captured all changes and tracked account activity. CloudHealth, a third-party tool was used to proactively discover risks and vulnerabilities and ensure policy enforcement.
- Enabled remedial action by configuring AWS SNS which alerts AWS Lambda to take remediation action under specific situations—if a port is open, SNS will notify Lambda and initiate action to close port automatically. If tagging for resource back-up is missing, Lambda will tag the resource; disable unauthorized access and even shut down non-compliant resources.
The customer is able to submit regular reports about compliance and incidence of non-compliance; and has no backlog in release compliance making the leap from DevOps to DevSecOps.
Architecture for Continuous Compliance on AWS Cloud
If you need help to make your deployments continuous compliant, reach out to us.







